 Business owners rely heavily on cloud-based services and technology today. When doing so, they must put robust security and privacy measures in place to protect sensitive information. Many organizations today rely on the Service Organization Control (SOC) 2 compliance audit, as this framework is widely recognized.
Business owners rely heavily on cloud-based services and technology today. When doing so, they must put robust security and privacy measures in place to protect sensitive information. Many organizations today rely on the Service Organization Control (SOC) 2 compliance audit, as this framework is widely recognized.
Table of Contents
What is the SOC 2?
Many people are unfamiliar with a SOC 2 compliance audit. However, anyone working with customer data must know how to manage it. A single breach could be the downfall of the organization. The standards set in place through SOC 2 reduce the risk of this breach happening.
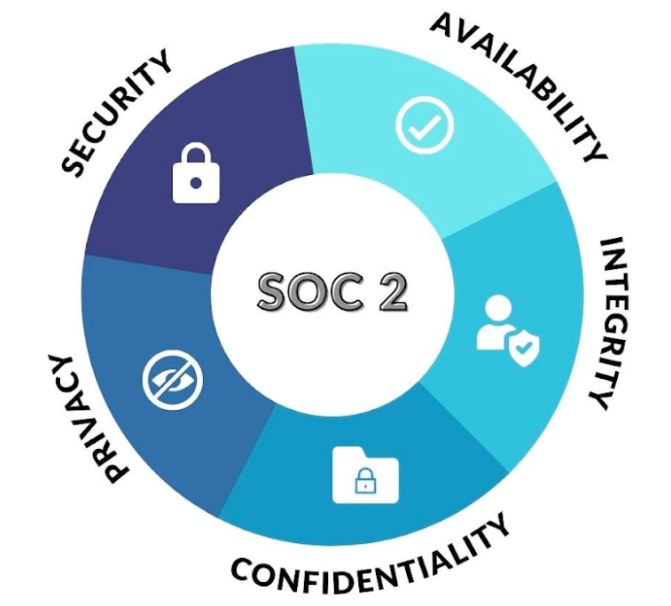
The American Institute of CPAs (AICPA) developed the set of standards known as SOC 2. These standards lay out the requirements for managing customer data. They are built around five trust principles: security, availability, processing integrity, confidentiality, and privacy. During a compliance audit, the organization’s internal controls and processes undergo a thorough examination. The examiner looks for any potential problems so they can be corrected before problems arise. Customers and stakeholders appreciate seeing the results of this audit, as it gives them confidence in the way their data is being handled. They know the organization is using industry best practices.
The Audit Process
Several steps make up the SOC 2 compliance audit process. The examiner initially determines the audit scope by identifying what must be evaluated as part of this process. The organization turns over detailed documentation of any policies, procedures, and internal controls related to the trust principles and the auditor conducts tests to ensure they are operating as intended. Upon completion of the audit, the examiner shares their findings. They provide information on where changes need to be made for better security. The organization must then develop and implement a remediation plan to address the problems.
The Five Trust Principles
Each trust principle is designed to improve the security and reliability of the company’s systems and processes. Security is focused on protecting the organization’s systems from unauthorized use or access. Availability refers to the ability of authorized users to access the systems and data as needed while processing integrity looks at whether the systems and processes work as intended. Confidentiality is essential to protect sensitive and proprietary information and privacy is needed to safeguard personal information.
The Benefits of SOC 2 Compliance
SOC 2 compliance comes with several benefits. Customers, stakeholders, and partners trust an organization more when it has taken this step. They know their data is being handled securely and reliably. This compliance provides the business with a competitive edge while reducing risks. The controls and processes that must be in place for SOC 2 compliance reduce a company’s exposure to security breaches and other operational risks. Organizations are encouraged to continuously review and improve their internal controls, which is always good as it will allow them to stay ahead of competitors.
Any service organization will benefit from a SOC 2 compliance audit as this framework helps guarantee its security and reliability in the digital age. Customers want to work with companies that put them first and this audit confirms a company does have its customers’ best interests at heart. The company must understand the purpose of an audit and its process to get the most from this examination. When it does, the organization will be able to engage in the audit and achieve success while remaining competitive as it aligns the company with these standards.






